Can you see your all your IT assets?
Most organisations can’t. That’s because traditional methods of asset management offer an incomplete view, resulting in poor security, operational inefficiency and unnecessary costs.
What’s going wrong?
Rebasoft provides a real-time asset inventory
It’s simpler, easier and covers more ground – meaning you can streamline your security and cut costs.
Scanless
Say goodbye to scheduling network scans. Rebasoft is ‘always-on’, so it’s always accurate, always up-to-date and there’s no “drift”.
Agentless
You never have to worry about incompatible devices, to Rebasoft it’s all the same – wether it’s network infrastructure, endpoints or IoT.
Break down silos
We don’t aggregate other programs’ data, we don’t serve it stale, we aren’t a point solution. It’s all fresh, native discovery for all your digital IT assets.
See.
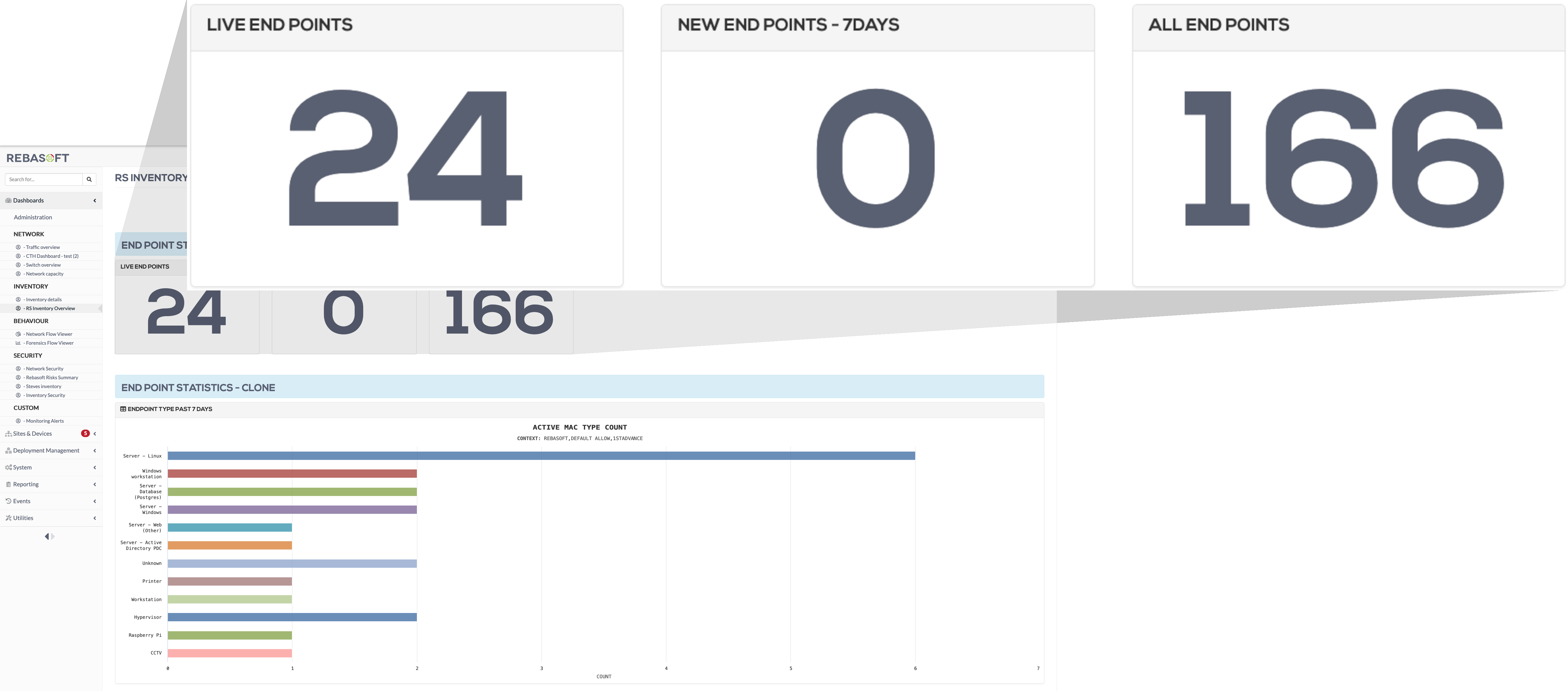
Asset discovery & inventory
Rebasoft uses passive network monitoring to build a real-time asset inventory. This feeds directly into other processes like secure configuration and vulnerability management – which means you can streamline your security, cut costs, reduce manual work and the need for integrations. Or you can integrate it into external systems via API.
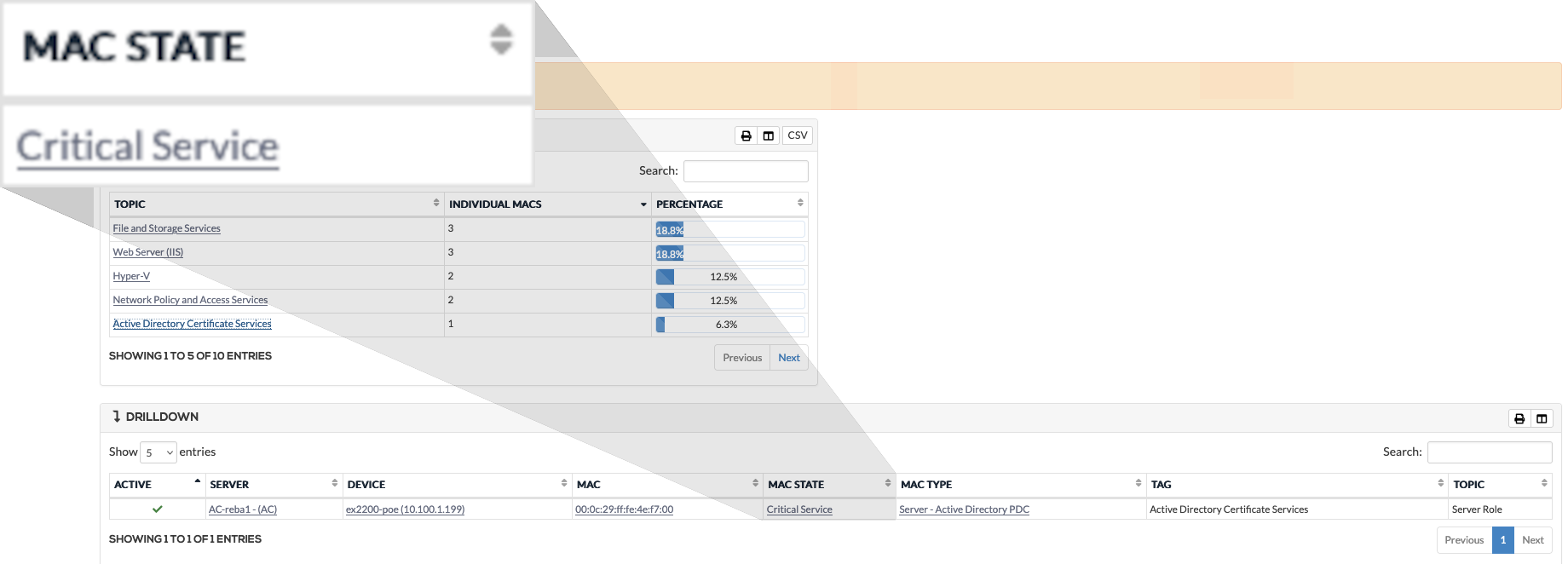
Criticality and prioritisation
Set BIA values to assets for better prioritisation.
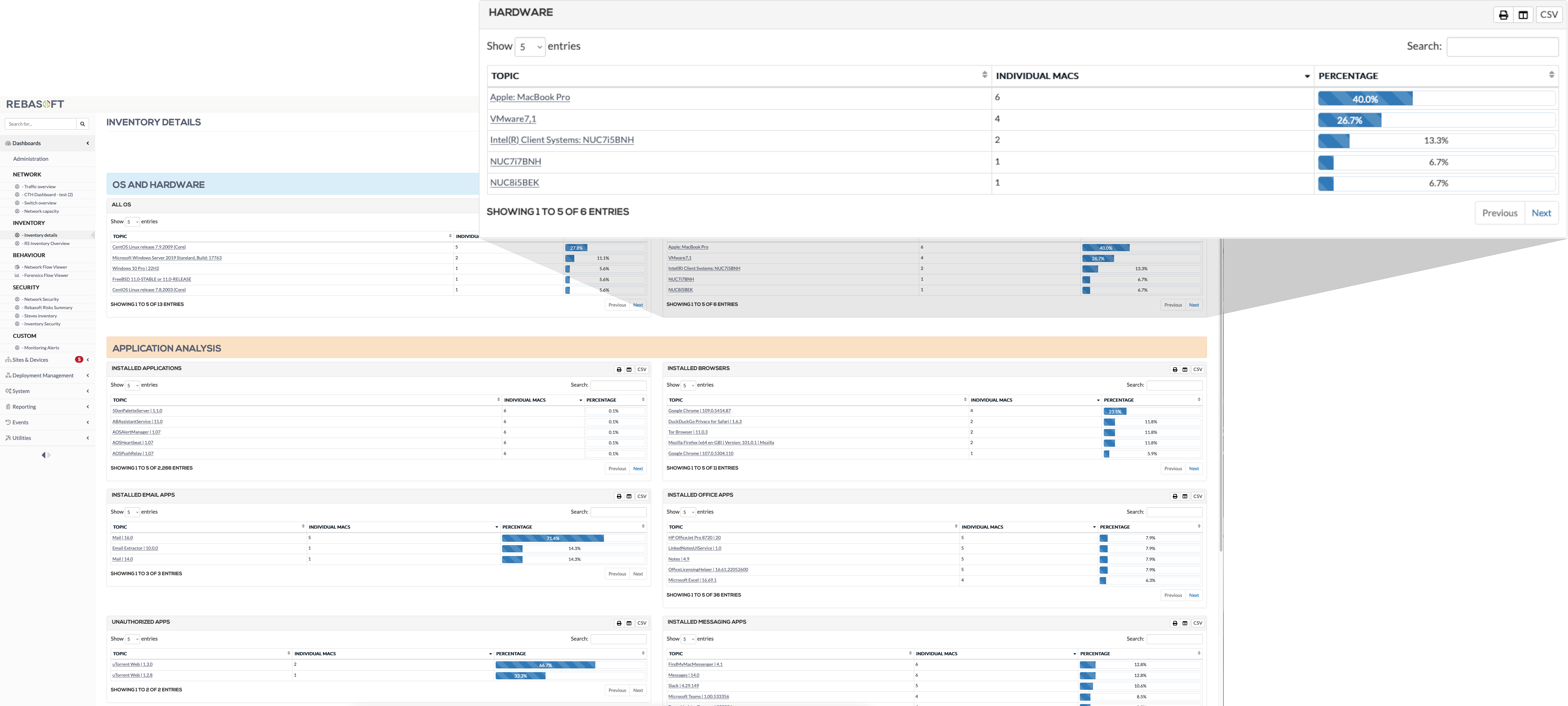
Device details
Feed this information into certification and compliance reports or integrate into external systems via API:
- Hardware model
- Location
- Operating system
- Installed applications
- Users, end-of-life and more
The Rebasoft Security Platform
Three core solutions, one unified platform
