IT teams are struggling to stay policy-compliant
Using a secure configuration tool that’s disconnected from the asset discovery process leads to inaccuracies and delayed mitigation.
Rebasoft can help
Fully integrated with the asset management system and the vulnerability management system you can streamline secure configuration and compliance – and cut costs while doing so.
Full Visibility
Natively built off the asset inventory, you can ensure accurate coverage and track changes in near real-time, streamlining the process.
Real-time data
The Rebasoft asset inventory is real-time, ensuring it accurately reflects the state of the environment, eliminating blind spots.
Prioritise
It’s natively integrated into the vulnerability management system, allowing you to accurately assess your security posture
Secure.
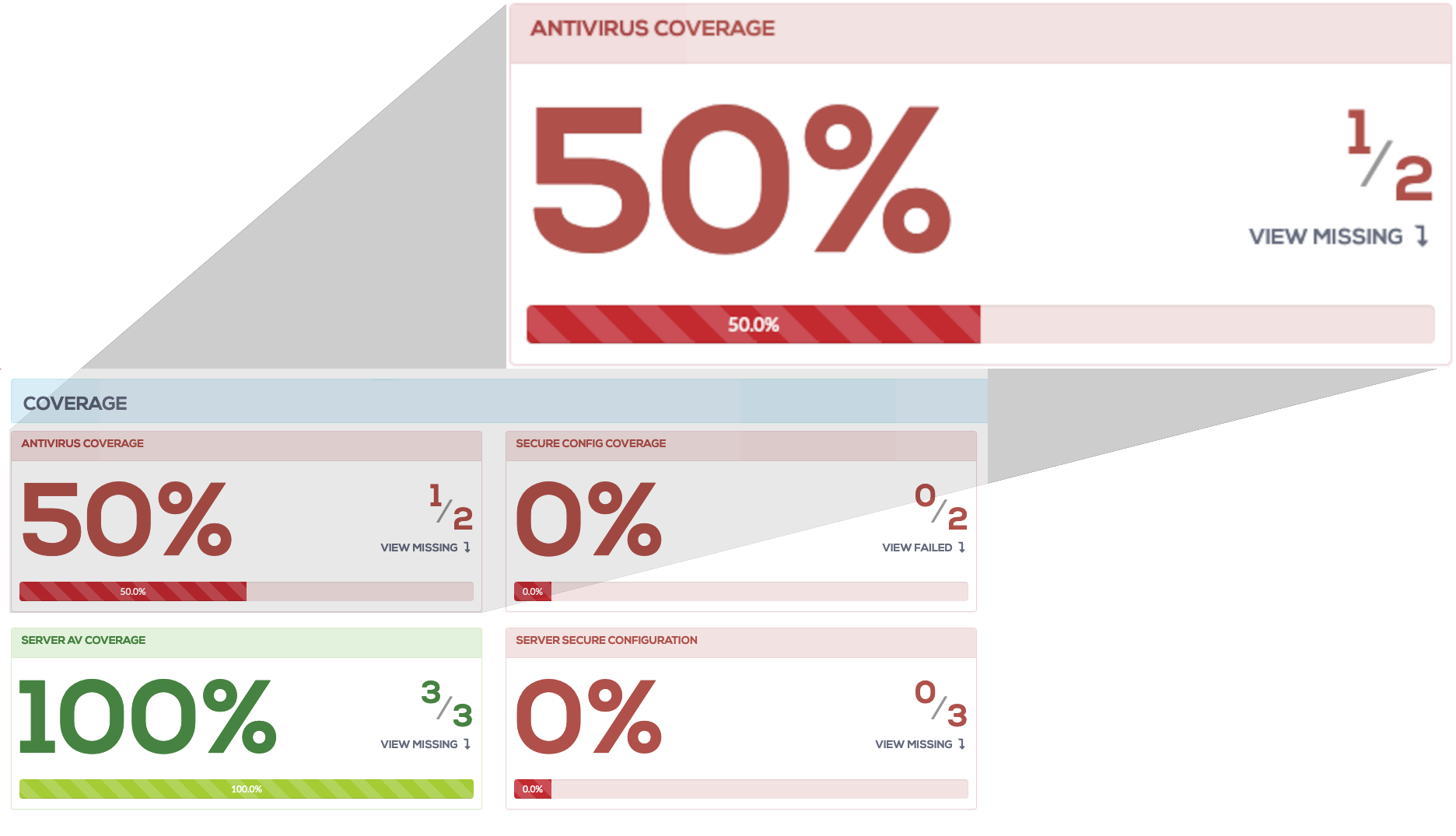
Secure configuration
Flexible, at-a-glance status of key security measures. Answering critical security questions like:
- Is AutoPlay disabled?
- Are users allowed to install their own apps?
- Are personal firewalls and disk encryption enabled?
- Are Linux servers recommended SSH access settings enforced?

Network perimeter security
The key to building a secure environment is ensuring the network is secured:
- Are network device management interfaces locked down to encryption methods?
- Are default passwords changed?
- Are third party connections identified and approved?
End-of-life
Track hardware and software status to plan for end-of-life:
- Identify all assets.
- Monitor their age.
- Monitor their performance.

The Rebasoft Security Platform
Three core solutions, one unified platform
