IT teams are struggling to stay ahead of vulnerabilties
Vulnerability management is still very much a manual task. The process takes too long because it requires multiple disjointed systems.
Network intensive scans
Vulnerability scanning is performance intensive, and causes a lack of productivity due to system downtime – and it only provides a “snapshot” of your vulnerabilities, essentially stale data.
Repeats and false positives
IT teams are often handed spreadsheets with 7000 line items and are told “go and fix it”. But many of these vulnerabilities are repeats and false positives, wasting precious time.
Lack of integration
Vulnerability scanning is often disconnected from the asset discovery process, meaning your IT team have to manually hunt down assets. Data is often siloed resulting in gaps and a delayed response.
Rebasoft can help
Rebasoft provides “always on”, asset-based vulnerability management. This helps you streamline your vulnerability management process so you can get ahead.
No scanning
Rebasoft matches vulnerabilities to assets automatically without needing scans – this means no system downtime. It does this daily, providing a continuous feed for quicker remediation.
Reduce repeats and false postives
You can choose to ignore a vulnerabilty if it doesn’t apply to you and Rebasoft will remember, it won’t show up next time, helping reduce workloads.
Natively integrated
Rebasoft uses the asset inventory as the foundation for vulnerability assessments. This streamlines the process and ensures you don’t miss vulnerabilities.
Defend.
The Rebasoft Defend. system doesn’t just provide enhanced vulnerability management. It provides other features to continuously defend your assets from threats.
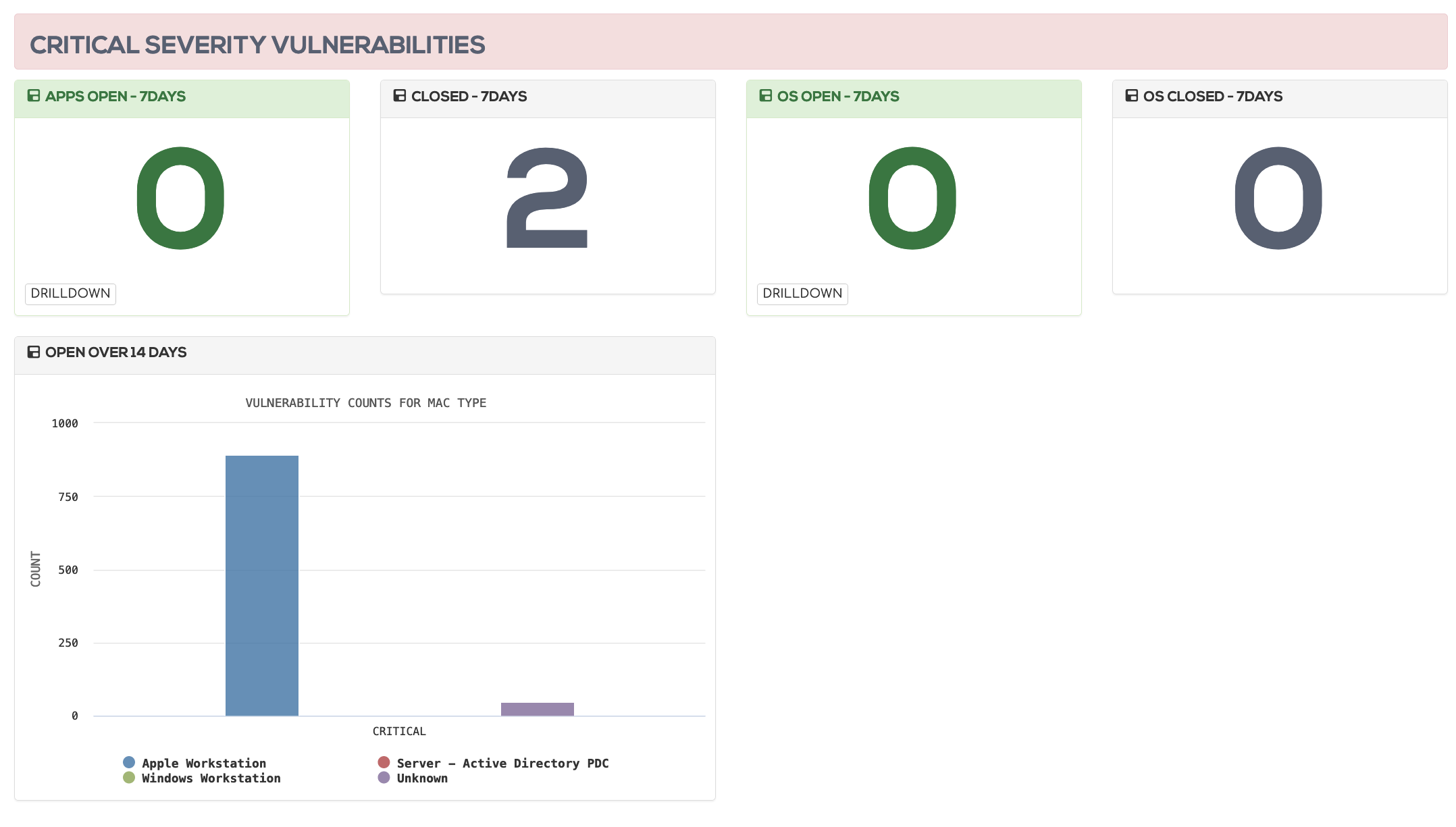
Vulnerability management
Rebasoft automatically matches assets to vulnerabilities without needing network scans and without needing agents. Because of the unique way we perform asset discovery, you can rely of Rebasoft to show you all your vulnerabilities for all your assets, all from one program, but you can also integrate it into other system easily via API.
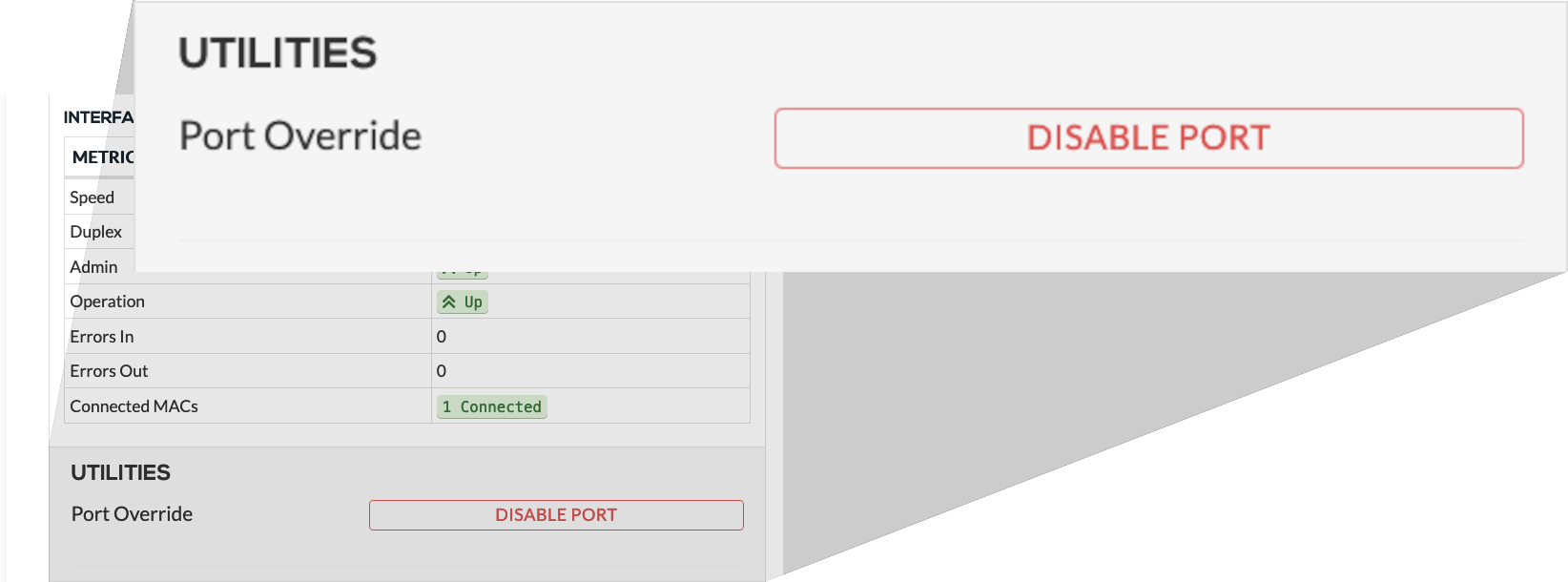
Network access control
Rebasoft can identify and isolate without needing agents or supplicants. There’s no network replacement or upgrades needed, only managable switches. Traffic monitoring supports non-user devices – no need to maintain mac whitelists.
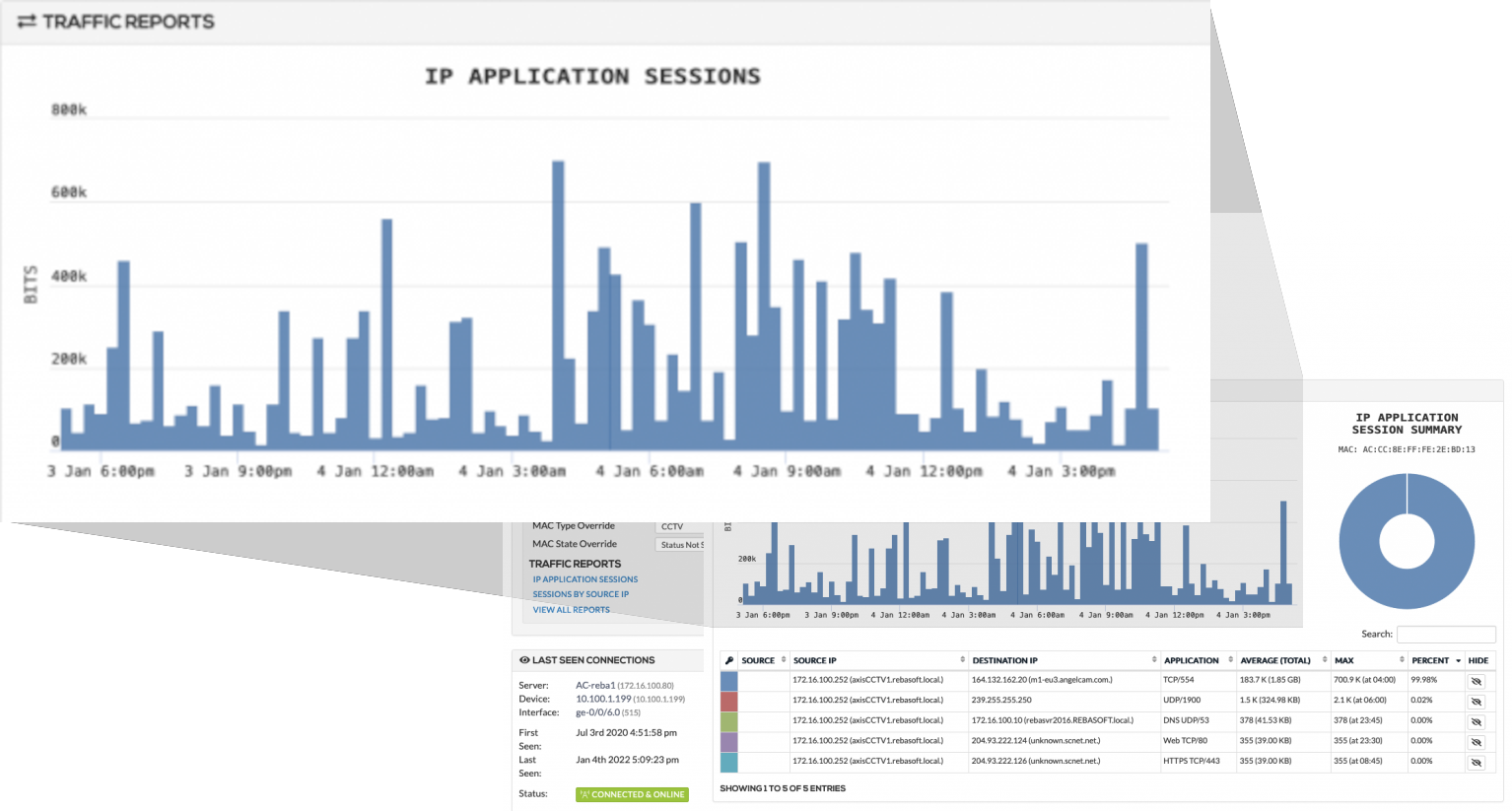
Traffic monitoring
Rebasoft is a network monitoring tool, it can indentify east-west lateral movement to detect malware. You can create traffic profiles, which is useful for ensuring IoT devices are behaving as expected. You can monitor Deny/Blacklisting to see attempts to circumvent security (e.g. with VPN, TOR) or connections to C&C control devices.
The Rebasoft Security Platform
Three core solutions, one unified platform